Video Tutorials
In our tutorial videos you will get an insight into workload automation with the BICsuite Workload Automation System. From the simple creation of a job and batch to conditional execution and different exit states to the automation of complex timescheduling tasks, you can see how easy it is to use our workload automation platforms.
Create a simple job
In the first part of our video tutorial series for BICsuite and schedulix beginners we show you how to open the gui in your browser, how to access the respective areas via the main menu and how to easily create and run a simple job.
Create a simple batch process
In this video, we will show how to create a simple batch in BICsuite that consists of four jobs that need to be executed interdependently.
Interventions in processing batches
In the third part of our tutorial series we demonstrate, how to monitor running batches and intervent in case of failures. You learn for example, how to rerun single jobs, cancel them or how to temporarily ignore dependencies.
Exit States: Definitions, mappings and profiles
This video starts a workshop in several parts about the conditional execution of jobs. One job within a batch should only run, if another job has actually loaded new data. In this video you learn to handle Exit-State-Definitions, -Mappings and -Profiles in BICsuite and you build up the conditions for the communication between jobs.
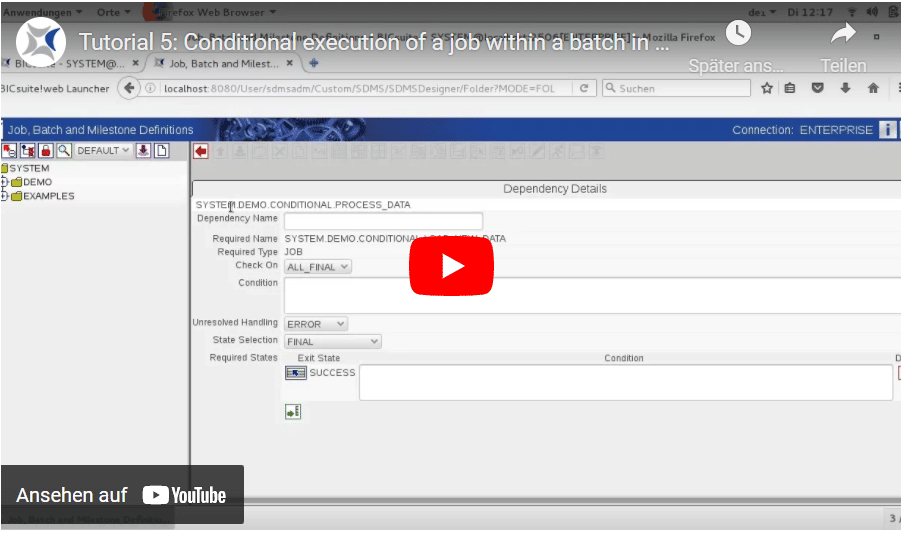
Conditional execution of a job within a batch
In this tutorial you create a batch consisting of the jobs ‘LOAD-NEW-DATA’ and ‘PROCESS-DATA’. The job ‘PROCESS-DATA’ should only run if the job ‘LOAD-NEW-DATA’ has actually loaded new data.
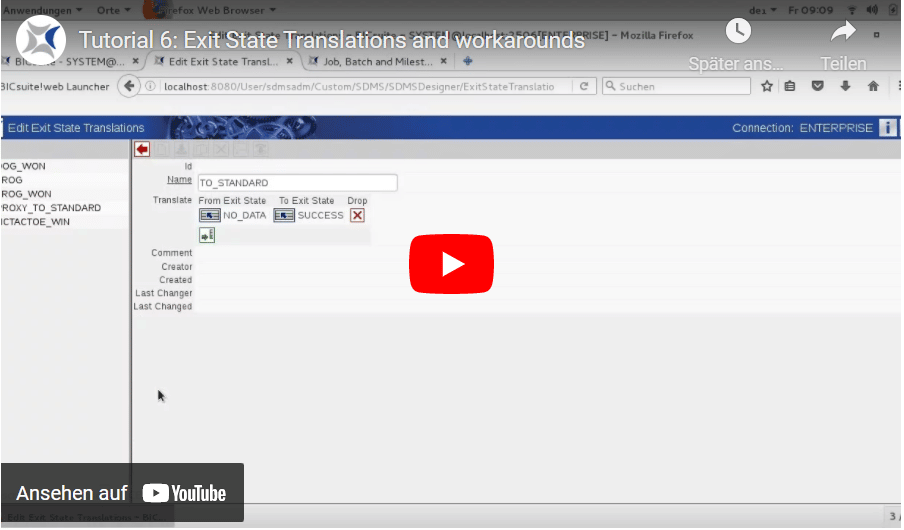
Exit State Translations and workarounds
That tutorial explains, how to handle in BICsuite and schedulix a small weak point in the result of the last video. Because the second job was skipped, the whole batch appeared with the Exit State SKIPPED. Here’s how to finalize the batch with SUCCESS.
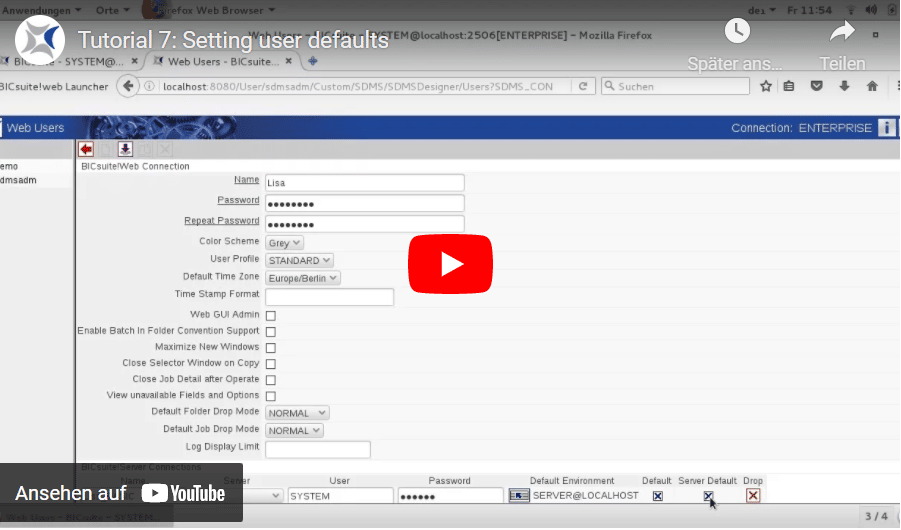
Settings user defaults
In this video you get known to the user settings of BICsuite and schedulix. You learn how to create a new user profile, define your defaults and add time zones to the selection list.
Time scheduling with different time zones
The video describes some basic time scheduling functions with the newly added time zones New York and Tokyo. We prepare three jobs to start in Munich, New York and Tokyo every day at 5 pm local time.
More time scheduling options
In that video we execute time scheduled jobs on specific days by changing the master schedules that we created in video tutorial number 8. The Munich job should run every Friday. The New York job has to run on the last Friday of the month, and the Tokyo job should only run when Friday falls on a 13th.
More calendar features for time scheduling
Here we demonstrate some of the advanced time scheduling features of BICsuite and schedulix. We are assuming that our company has branches in Hamburg, Berlin and Munich. Each branch has its own additional public holidays. A job should only run if all the branches are working. A second job will always run if at least one of the three branches is working.
Discover the Highlights
Learn more
Browse our growing collection of articles, explainer videos, and tutorials to discover practical insights and best practices for workload automation with schedulix and BICsuite.
ExploreAny questions?
Please feel free to reach out to us if you have any questions or require further information. Our team is here to assist you.
Contact us↑ Go to Top